Election Cybersecurity is About More than Just Voting Machines
While the Senate debated whether to impeach former President Trump for undermining democracy, the federal Election Assistance Commission (EAC) was hard at work securing the future of American democracy. For the first time in 15 years, the EAC voted unanimously to adopt a new version of the Voluntary Voting System Guidelines (VVSGs), a comprehensive set of standards which states can use for their elections.
While the updated VVSGs are essential for election security, their scope is limited to “voting systems,” the hardware and software used to cast and count ballots.
But election cybersecurity is about more than just voting machines.
That’s why CDT, in collaboration with the Konrad-Adenauer-Stiftung (KAS) foundation, issued a new report today, An Agenda for U.S. Election Cybersecurity, that considers election infrastructure components beyond voting systems. As shown in the below figure, voting systems are just one component of election infrastructure that must be secured.
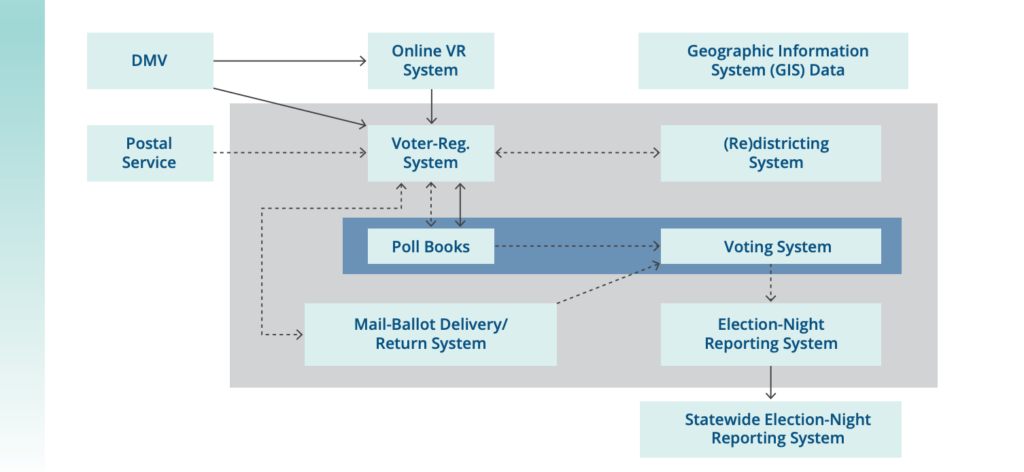
Reproduced from Stewart III, Charles. “The 2016 U.S. Election: Fears and Facts About Electoral Integrity.” Journal of Democracy 28:2 (2017), p. 56, Figure 2. © 2017 National Endowment for Democracy. Reprinted with permission of Johns Hopkins University Press.
Source: This schematic of voting information-system architecture is based on the work of Merle King. For King’s full schematic, see https://www.nist.gov/system/files/documents/itl/vote/tgdc-feb-2016-day1-merle-king.pdf#page=14.
In the report, we describe best practices and policy considerations for election officials, members of Congress, and federal agencies, on the following components of election infrastructure:
- Voter registration systems
- Poll books
- Voting machines
- Absentee and mail-in voting
- Tabulation and reporting
- Individuals involved in elections
The cybersecurity of non-voting systems is just as critical to the integrity of the vote. For example, a cyber attacker could wreak havoc if they were to successfully attack state voter registration systems at a critical time. We got a sense of what that could look like last year when, on the last day for Floridians to register to vote, pop star Ariana Grande tweeted out a note encouraging her followers to register, causing traffic to spike up to 1.1 million requests per hour.
The traffic, and misconfigured servers, led to the system becoming unavailable, preventing voters from being able to register and leading to eventual litigation. Had this been the result of an intentional attack—or had it been paired with a disinformation campaign spreading lies about the provenance or purpose of the attack—it could have more seriously undermined trust in the election.
Another component of election infrastructure that must be secured is poll books. Instead of signing voters into a physical poll book, states are increasingly using internet-connected e-poll books to check in voters. These have several advantages, including: speeding up the check-in process; enabling real-time updates to the voter registration database, including registering voters as they check in; and enabling a vote center model in which voters of a jurisdiction can show up at any polling place.
But because e-poll books must be connected to the internet, they create cybersecurity vulnerabilities. Specifically, if a cyber attack successfully targeted an e-poll book system, in-person voting could be halted for hours. This elevates the importance of securing these systems and ensuring that jurisdictions, to the extent possible, have paper backups on hand.
One major improvement Congress could make to election security would be to consistently fund the Election Assistance Commission at higher levels. For one thing, more funding could streamline the VVSG updating process and ensure that they are more responsive to current conditions. The EAC could also expand its scope, potentially providing guidance for states on best cybersecurity practices on non-voting systems like e-poll books.
The EAC has shown an interest in this kind of program, partnering with the Center for Internet Security to pilot a program focused on securing non-voting election technology. This is a promising venture, and we support the EAC receiving funding sufficient to help secure even more of American election infrastructure.
Despite election experts describing the 2020 election as the most secure in American history, many voters distrust the results. A functioning democracy depends on widespread trust, and that in turn depends on secure elections infrastructure. While there were no major successful cyber attacks on our election infrastructure last year, we should not rest on our laurels. We hope that the best practices and policy considerations we offer provide an agenda for ensuring the resilience of American democracy.