Do Ballot Barcodes Threaten Election Security?
Bogus conspiracy theories about the 2020 election have been repeatedly debunked. But that hasn’t stopped election conspiracy theorists from attempting to gain influence in election administration, either as low level poll workers or as top state election officials. The infiltration of election deniers into positions of power in administering elections poses a grave danger to American democracy: the possibility that an insider will manipulate election systems in order to bring about a desired election outcome. This elevated insider threat makes it more important than ever that our voting systems are resilient to attack and manipulation.
Many 2020 conspiracy theories concerned the voting systems in Georgia, where President Trump focused intensely on discrediting the results. That year, Georgia used ballot marking devices (BMDs) for the first time, for all in-person voters. BMDs are touch screen computers that print out a paper ballot—a major improvement over the paperless machines Georgia had previously been using. Now, voters could physically inspect the record of their vote, rather than be forced to trust the machines to record the votes accurately.
BMDs are widely used in U.S. elections and offer several benefits over hand-marked paper ballots (HMPBs). For instance, because they have a variety of user interface options, BMDs enable voters with visual or motor disabilities to vote independently and privately when they might otherwise be unable to do so with a HMPB. But all computerized systems are susceptible to attack. Therefore, the use of BMDs—particularly by large numbers of voters who do not require them for accessibility reasons—has been criticized as posing a serious security threat to elections. The balance between these benefits and risks should be carefully considered.
The “inconsistent barcode” / “text swap” attack
An upcoming CDT report will take a close look at some of the arguments made about the security of BMDs. But, in this post, we want to examine one particular characteristic of most BMDs: the barcodes on the paper ballots that they produce. After a voter has finished making their selections on the machine’s touch screen, the BMD will print out their selections in human-readable text for them to review. Most BMDs, such as the Dominion ImageCast X used in Georgia, will additionally encode those selections in a 1- or 2-dimensional barcode (i.e., QR code).

The benefit of encoding selections in a barcode is that ballot scanners can read them quickly and accurately. But some have said that encoding voter selection in a barcode is problematic—a ballot from the ImageCast X, for example, contains two records: the human-readable record and the machine-readable record. This lends itself to an attack called the inconsistent barcode attack, in which a hacked BMD alters the vote encoded in the barcode—and therefore the vote recorded by scanners—but leaves the human-readable portion intact. A voter could not detect this attack, because the ballots would appear correct to them. An advisory published today by the federal Cybersecurity and Infrastructure Security Agency recommends mitigating specific vulnerabilities that could lead to this kind of attack. It then notes that the ImageCast X can be configured to print ballots that do not have barcodes—presumably instead printing a filled-in bubble ballot. The Clear Ballot ClearAccess BMD, for example, produces this kind of ballot.
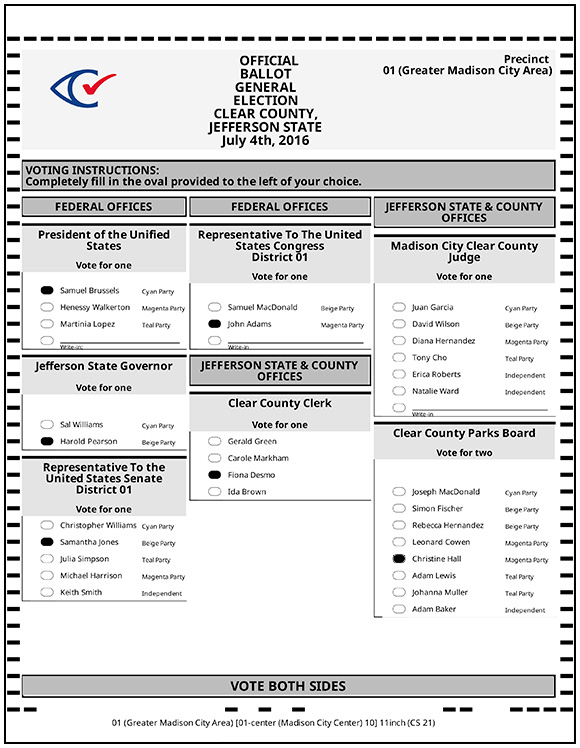
Are these “bubble ballots” immune to the inconsistent barcode attack?
Not really.
When tabulating these bubble ballots, scanners interpret only the position of the filled bubbles, entirely ignoring the text next to the bubbles. In other words, these ballots also contain both a human-readable record (the text next to the filled bubbles) and a machine-readable record (the positions of the filled bubbles). A hacked BMD that prints bubble ballots might therefore switch the position of the text as well as the position of the filled bubble. This “text swap attack,” while perhaps easier to detect, is essentially the same as the inconsistent barcode attack—an attack on the BMD that exploits how the scanner will interpret the ballot.
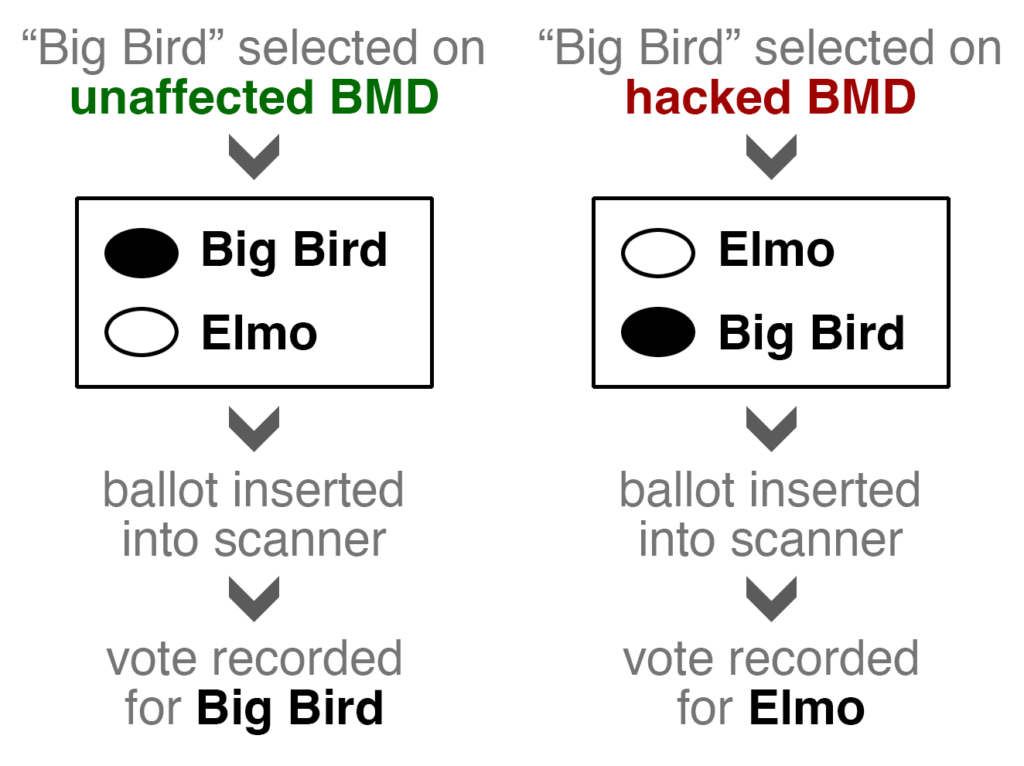
Even HMPBs are vulnerable to this kind of attack. Whether ballots are printed ahead of time or printed on demand for each individual voter, it is possible that a voter could be handed a ballot that swaps the position of candidate names, which few or no voters would notice.
So what are the solutions?
The primary solution: Voter verification and risk-limiting audits
The most important way to mitigate this attack—and many other assaults on elections—is to ensure that voters verify their ballots, and that the human-readable portions are routinely inspected by risk-limiting audits (RLAs). If every BMD-using voter inspects the human-readable portion of their ballot before casting the ballot, then the physical record will reflect every voter’s intent, regardless of whether the BMDs were hacked. And then a risk-limiting audit, by randomly sampling ballots, inspecting and tallying only the human-readable portion, can efficiently determine whether the outcome is correct.
Of course, ensuring voter verification is no simple task. It seems that, unless instructed to, voters are unlikely to verify their ballots. But there may be interventions—in terms of voter instruction and the design of the overall voting experience—that improve verification rates.
Nor is it a guarantee that all races will be subject to a RLA. While RLAs have been increasing in popularity, most states do not conduct them. And RLAs cannot simply be implemented overnight. Because RLAs depend on sampling ballots at random across a state or district, the manner in which ballots are stored, organized, and numbered, is important. Election officials may have to do several pilot tests in order to establish procedures that work best for them.
Although it is essential to strive for high rates of voter verification and frequent risk-limiting audits, we cannot count on them for every election. We therefore propose a supplemental way to mitigate the “inconsistent barcode” / “text swap” attack.
A supplemental improvement: Optical character recognition for ballot scanners
As long as ballots are encoded in both a voter-verifiable form (i.e., printed text) and in a machine-readable form (i.e., in a barcode or in the position of filled bubbles), there is a potential risk that the machine-readable form could be altered, affecting the electronic tabulation. However, the risk can be eliminated if the only record of the vote is the printed text and if tabulators interpret that record in the same way as voters. In such a system, optical scanners would have to read and interpret the printed text (i.e., the names on a summary ballot, or the names next to filled bubbles on a bubble ballot) using optical character recognition (OCR) technology. To our knowledge there is only one voting system in use in the U.S. that uses OCR to scan ballots: the Hart InterCivic Verity Duo system, which is deployed primarily in Kentucky and Texas. Other vendors should consider offering systems that only print and scan voter choices in human- and machine-readable text.
Some have suggested that OCR cannot match the speed and accuracy of barcode-scanning. But OCR should be readily achievable in the polling place and at counting sites with modern hardware and software. The U.S. Postal Service, for instance, has since 1965 used OCR to sort mail. And reading printed ballots (along with filled bubble location), while not trivial, should be an easier task than reading handwritten addresses; with the exception of write-in candidates, the text is computer-printed and the possible text strings can be known in advance by the scanner.
Implementing OCR on voting systems is merely a supplemental improvement—not an alternative to increased voter verification and RLAs. Voter verification is still essential, because a hacked BMD could still produce an incorrect ballot in a way that is visible to the voter (e.g., in the example above, filling in the bubble next to “Elmo” even when the voter selected “Big Bird”). And RLAs are still essential because they protect against hacked or defective scanners and tabulators—OCR does not.
But we think that this is a promising area for further research and product development. In addition to eliminating attacks on ballot barcodes, it may boost voter trust to remove non-voter-verifiable information from the ballot.
TL;DR
Ballots that encode voter choice in barcodes (or even in the position of filled bubbles) may potentially pose a threat to election security. One way to address this is to have tabulators use OCR to interpret ballots. But OCR is simply no substitute for maximizing the number of voters who verify their paper ballots and ensuring strong post-election audits on the voter-verified text.
If the 2024 elections are run by people who have campaigned on election denialism, we will have a serious election security threat on our hands. Ensuring voter verification and strong risk-limiting audits will certainly be an essential protective measure. But there are so many opportunities for motivated insiders to manipulate elections that we will also have to redouble our efforts to ensure that elections are transparent, well-monitored by members of each party, that the chain of custody of ballots is preserved, and that election officials do not abuse their powers for partisan gain.