Cybersecurity & Standards, Elections & Democracy
Election Cybersecurity 101 Field Guide – DDoS Attack Mitigation
CDT’s Election Cybersecurity 101 Field Guides are a series of short, simple, usable guides intended to help election administrators and staff better understand key concepts in cybersecurity.
Keeping Your Website Available Online
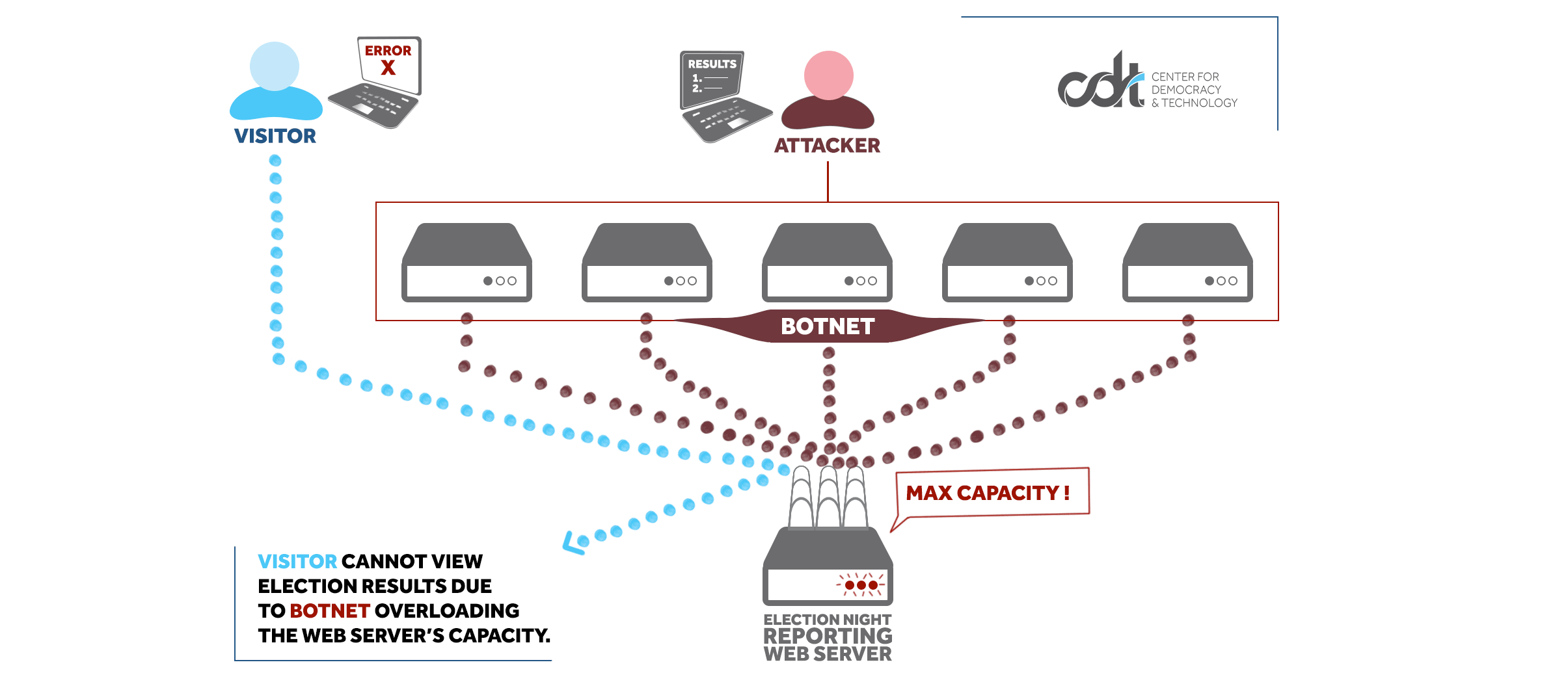
- The greatest benefit of making certain parts of the election process available online is efficiency: it makes it faster and easier to register to vote, verify the status of a mail-in ballot, and check results on election night. Unfortunately, connecting those systems to the Internet also makes them targets for malicious actors looking to disrupt the election process by blocking access to election-related websites. A very effective method to block access to a website is to overwhelm the website’s server with requests from fake visitors. When too many requests are sent to the website server other requests from legitimate visitors are turned away (or denied). It is the digital equivalent of crowds of shoppers trying to rush into a retail store the day after Thanksgiving – there are only so many doors into the store and that prevents everyone from entering at the same time. When this happens maliciously it is known as a Denial-of-Service (DoS) attack.
- Generating enough requests to simulate traffic that is thousands of times larger than normal requires a lot of computers. When a malicious actor controls a large number of computers (a botnet) making repeated requests it is called a Distributed Denial-of-Service (DDoS) attack. A DDoS Mitigation service can act as a shield and a filter to block the large number of malicious requests while still allowing legitimate visitors to access your website normally.
- This kind of attack happened to Knox County, TN in their 2018 primary when its election night results reporting website was overwhelmed by both legitimate and malicious traffic due to interest in a popular mayoral race. No votes were changed but the perception that the “election system was down” raised concerns in voters locally and nationally that a larger attack was underway.
Why DDoS Mitigation is Important
- DDoS attacks will remain a critical threat to public-facing election systems for the foreseeable future because the attacks are easy to start and very difficult (sometimes impossible) to withstand for more than a few hours or a couple days, given the very large amount of traffic they can generate. Malicious actors can infect insecure computers and IoT devices (such as security cameras and DVRs) in order to control and direct them to attack a target. Improving DDoS defenses is the only practical way slow the effectiveness of this kind of attack until computers and IoT devices become more secure by default.
- Having DDoS Mitigation in-place before an attack helps establish a baseline for normal activity so that spikes in traffic or requests from unusual locations can be identified. Passing along that technical data through information sharing coalitions like the MS-ISAC or EI-ISAC can give other jurisdictions a heads-up about suspicious activity, and give them precious information and time for their own response.
For other field guides, more resources, and info on what CDT is doing to help election officials, check out our Election Security campaign.


