Don’t Get Hijacked on the ‘Net: Firesheep and HTTPS
This week, a piece of software called Firesheep reminded us of how important it is to browse the Internet securely.
Firesheep is a very user-friendly Firefox add-on that allows its user to snoop on unsecure connections on a local network (such the Wi-Fi at your local coffee shop) and hijack services being used on that unsecure connection. This means that, by default, a visit to Facebook, Twitter, Flickr, and other popular services might be enough to give anyone using Firesheep access to your account. Just look at how simple the Firesheep snooping program is:
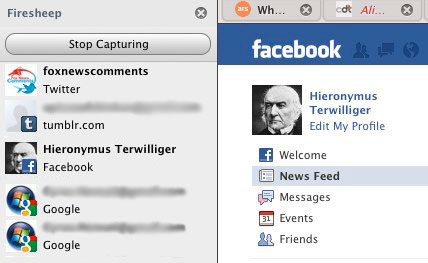
Above you can see Firesheep from the attacker’s eyes. The menu on the left shows unsecured connections on the network. All the attacker needs to do is click on the account they want to use. It’s scary stuff.
The solution to this problem isn’t fancy or new. An encrypted connection between you and a website can provide a substantial measure of protection. This encryption technology is colloquially referred to as HTTPS and is regularly used by payment processors, banks, and, increasingly, many other types of websites. By encrypting your connection, you’re protected from snoopers (probably, see below).
Given the increasing prevalence of easy-to-use snooping programs like Firesheep, CDT offers the following guidance to web platforms and consumers.
Popular Web Platforms Should Enable HTTPS by Default
It has been said many times before, but it bears repeating: Popular websites should enable secure connections by default to protect their users.
At the time of this writing, Facebook, Twitter, Flickr, and many other popular services do not enable secure connections by default, leaving their users vulnerable to simple attacks such as Firesheep.
Happily, some services have already fixed this problem. For example, earlier this year, Google made HTTPS encryption the default for Gmail, its popular webmail service. Gmail’s engineering director noted that “[u]sing https helps protect data from being snooped by third parties, such as in public wifi hotspots.”
Other web platforms should follow suit. The technology to do so is readily available and cost effective.
Users Should Learn to Recognize HTTPS and Make Informed Decisions
It only takes a simple glance to know when you’re browsing securely.
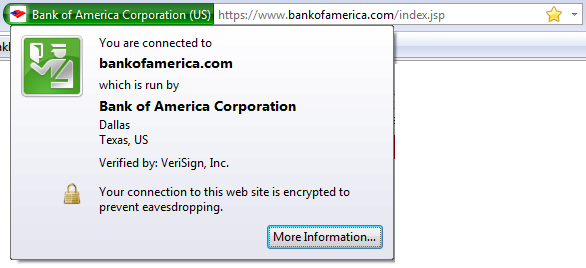
First, you can see when you’re using a secure connection by checking for the “https://” before the web address. Additionally, most modern browsers will give some additional indication to the left of the web address, such as a lock or colored bar. (On Firefox, the lock appears on the bottom of the frame.)
Second, you can see whether or not your secure connection has been certified by a certificate authority (CA) by hovering your mouse cursor over the area to the left of your address bar. A CA is a trusted third party, such as VeriSign or DigiCert, that vouches for the identity of the website you’re connecting to.
HTTPS isn’t always necessary, of course. If you’re not dealing with personal or financial information – for example, if you are just reading a blog – HTTPS likely isn’t a necessity.

While HTTPS can offer a meaningful boost to your online security, the system isn’t perfect. A secure connection is important, but a secure connection to the wrong party may lead you to disclose information that you might otherwise like to keep private.
HTTPS Isn’t Perfect: Don’t Always Take a Certified Secure Link at Face Value
Not all Certificate Authorities take the same care in vetting the online services to which they issue certificates. Many even delegate their certificate-issuing authority to third parties, which can then certify secure sites in the CA’s own name. Once delegation is taken into account, there are hundreds, possibly thousands of certificate providers capable of testifying to your browser that a connection to a website is secure.
Some of these providers are not particularly trustworthy, but it’s difficult for you, the user, to figure out which aren’t and to tell your browser to avoid certificates issued by those CAs or delegates. There are a number of proposals discussing how best to address this problem, such as reducing CA delegation and updating software to empower uses to easily make their own decisions. For now, however, it’s baked into your browser.
And you still have to be careful to avoid phishing and other scams. A link in an otherwise suspicious email is just as likely to be bogus if it has the “https://” prefix.
Despite these limitations, we should all use HTTPS if available and demand it from our favorite online services.


