Proposed Info Sharing Legislation Could Worsen NSA Surveillance
On June 4, documents disclosed by Edward Snowden revealed that the government uses cyber threat signatures and malicious code as the basis for collection occurring under Section 702. This raises new concerns regarding the Cybersecurity Information Sharing Act (CISA, S. 754), and demonstrates that passing this legislation could increase the controversial collection and use of communication that occurs pursuant to Section 702.
CISA permits companies to share threat signatures with the government, and requires that this information be immediately and automatically forwarded to the NSA. The new disclosures show that these signatures can then be used as “selectors” under the NSA Section 702 upstream program, with communications containing the signatures grabbed directly off the Internet backbone. Databases containing those communications can then be queried to find Americans’ information, and forwarded to domestic law enforcement agencies to initiate and aid in the investigation of any crime. As Congress considers legislation that could expand the number of communications containing threat signatures the NSA collects without a warrant, it should consider reforms to Section 702 that will close loopholes and restore due process protections.
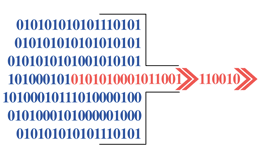
Identification of Cyber Threats
Company identifies malicious code signatures.


Sharing with DHS
Company shares malicious code signature with DHS, as authorized by CISA.


Auto-Sharing with NSA
CISA requires malicious code signatures shared with DHS be automatically forwarded to NSA.
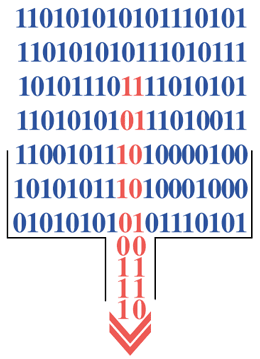
Cyber-Surveillance Dragnet
NSA creates a dragnet based on the malicious code signatures, and collects all Internet traffic and communications going into and out of the U.S. that include that signature into a government database.


Backdoor search for Americans
NSA, CIA, and FBI can query this database of communications collected – without a warrant – and deliberately gather Americans’ communications, even if they were only victims of malicious hacking.


Warrantless Investigation of Minor Crimes
Intelligence agencies can take Americans’ communications it searched for and share them with enforcement agencies (DEA, ATF, IRS, etc.) to initiate investigation of any crime.